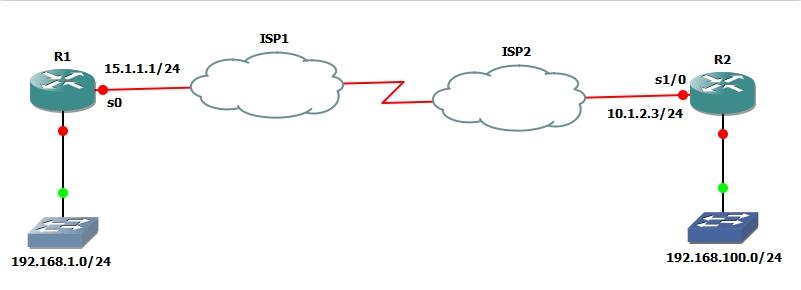
Here you can see two company locations are interconnected through public internet using cisco router R1 and R2 ( the perimeter routers). I am configuring IPsec VPN (secure VPN ) between these sites . The protected networks are 192.168.1.0/24 and 192.168.100.0/24 . Ie interested traffic is generated between these private networks. Means only traffic between these private networks are encrypted.
Router R1 configurations
Phase 1 configuration
a) ISAKMP Policy configurations
#crypto isakmp policy 10
#encyption 3des
#hash Md5
#group 2
#authentication pre-share
b) Pre-shared authentication key
#Crypto isakmp key cisco123 address 10.1.2.3
c) Define interesting traffic
#access-list 100 permit ip 192.168.1.0 0.0.0.255 192.168.100.0 0.0.0.255
Phase 2 configurations
d) Ipsec parameters
#crypto ipsec transform-set WAN_SET esp-3des esp-md5-hmac
e) Define crypto map
#crypto map WAN_MAP 1 ipsec-isakmp
#set peer 10.1.2.3
#match address 100
#set transform-set WAN_SET
f) Applay this map to interface
#int s0
#crypto map WAN_MAP
Router R2 configurations
Phase 1 configuration
a) ISAKMP Policy configurations
#crypto isakmp policy 10
#encyption 3des
#hash Md5
#group 2
#authentication pre-share
b) Pre-shared authentication key
#Crypto isakmp key cisco123 address 15.1.1.1
c) Define interesting traffic
#access-list 100 permit ip 192.168.100.0 0.0.0.255 192.168.1.0 0.0.0.255
Phase 2 configurations
d) Ipsec parameters
#crypto ipsec transform-set WAN_SET esp-3des esp-md5-hmac
e) Define crypto map
#crypto map WAN_MAP 1 ipsec-isakmp
#set peer 15.1.1.1
#match address 100
#set transform-set WAN_SET
f) Applay this map to interface
#int s1/0
#crypto map WAN_MAP